Setting up SCIM - Azure (Microsoft Entra ID)
This article describes how to set up SCIM Support on Security Journey in Azure.
What is SCIM?
SCIM is an open standard for automating user provisioning across domains, reducing the time and complexity typically associated with onboarding.
-
It removes the need for manual user management and minimizes human error, meaning program admins can spend more time with learners
-
Automatic syncing & updating of learner attributes
Prerequisites
In order to set up SCIM on Security Journey with Azure Active Directory, you will need:
Security Journey
-
An account with Admin privileges
-
SSO enabled in the Admin Settings
Azure (Microsoft Entra ID)
-
A user with Microsoft Entra ID Admin Center privileges
-
Existing SSO SAML 2.0 Application setup for Security Journey
Supported Features
Our SCIM Integration support the following features:
-
Create Users
-
Update User Attributes
-
Deactivate Users
Configuration Steps
-
Use the Microsoft Entra admin center to view and manage all applications that are configured for single sign-on in your organization.
-
Sign in to the Microsoft Entra admin center as at least a Application Administrator.
-
Browse to Identity > Applications > Enterprise applications.
-
A list of all configured apps is shown, including apps that were added from the gallery.
-
Find Security Journey from your list of Enterprise applications.
-
If SSO is not yet configured, follow the steps to setup SSO in Azure.
-
-
Select Provisioning to manage user account provisioning settings for the selected app.
-
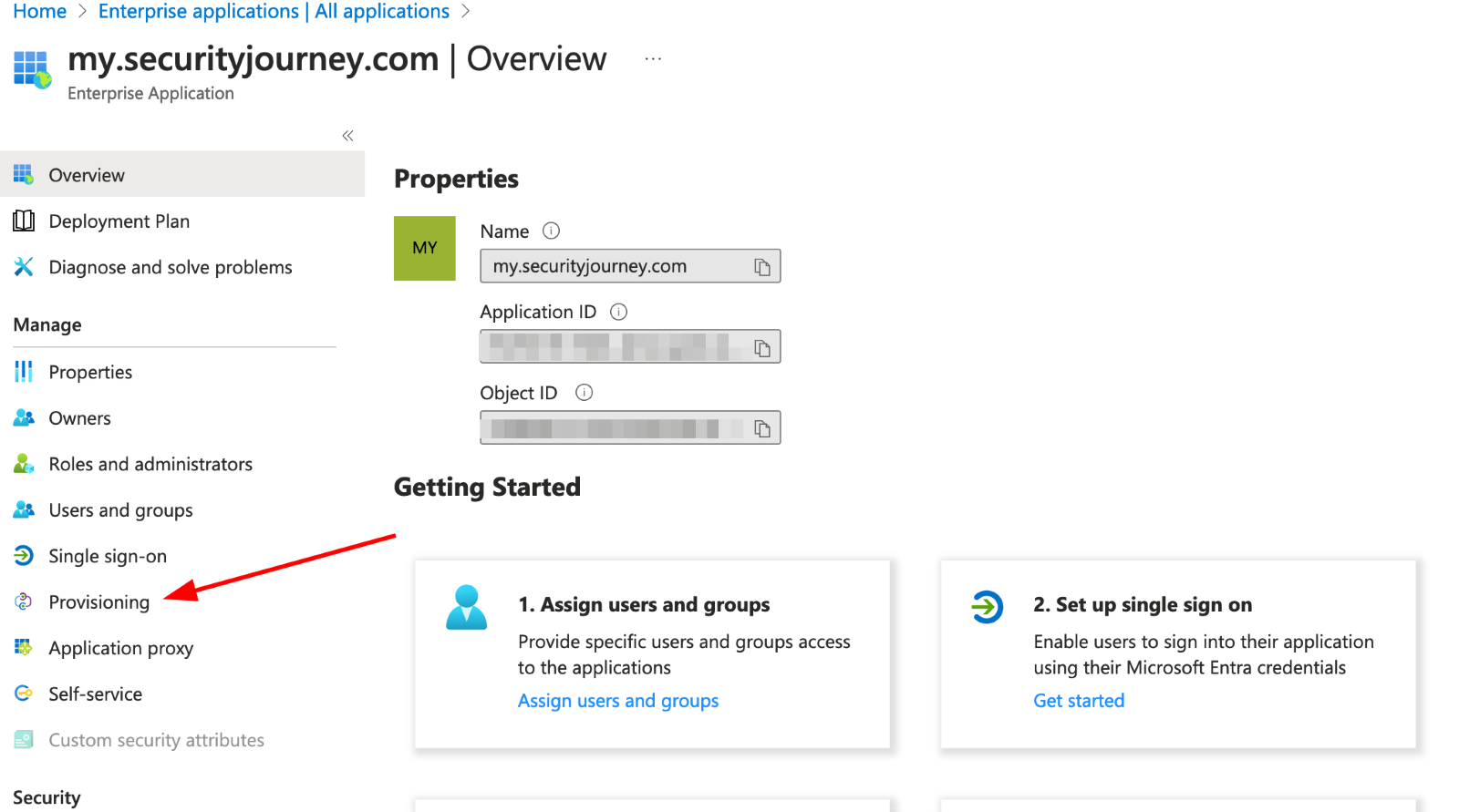
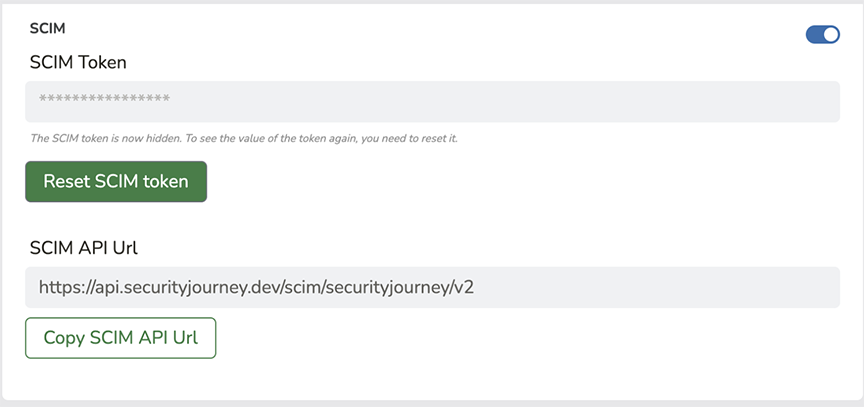
2. Once in the setup flow, you will need to login to Security Journey and navigate to More > Admin > Settings > SCIM:
-
Generate new SCIM Token and copy
-
Copy SCIM API URL
3. From here, you will go back to the Microsoft Entra ID Admin Center and enter the URL and SCIM API key and test the connection. A modal will popup indicating success or failure.
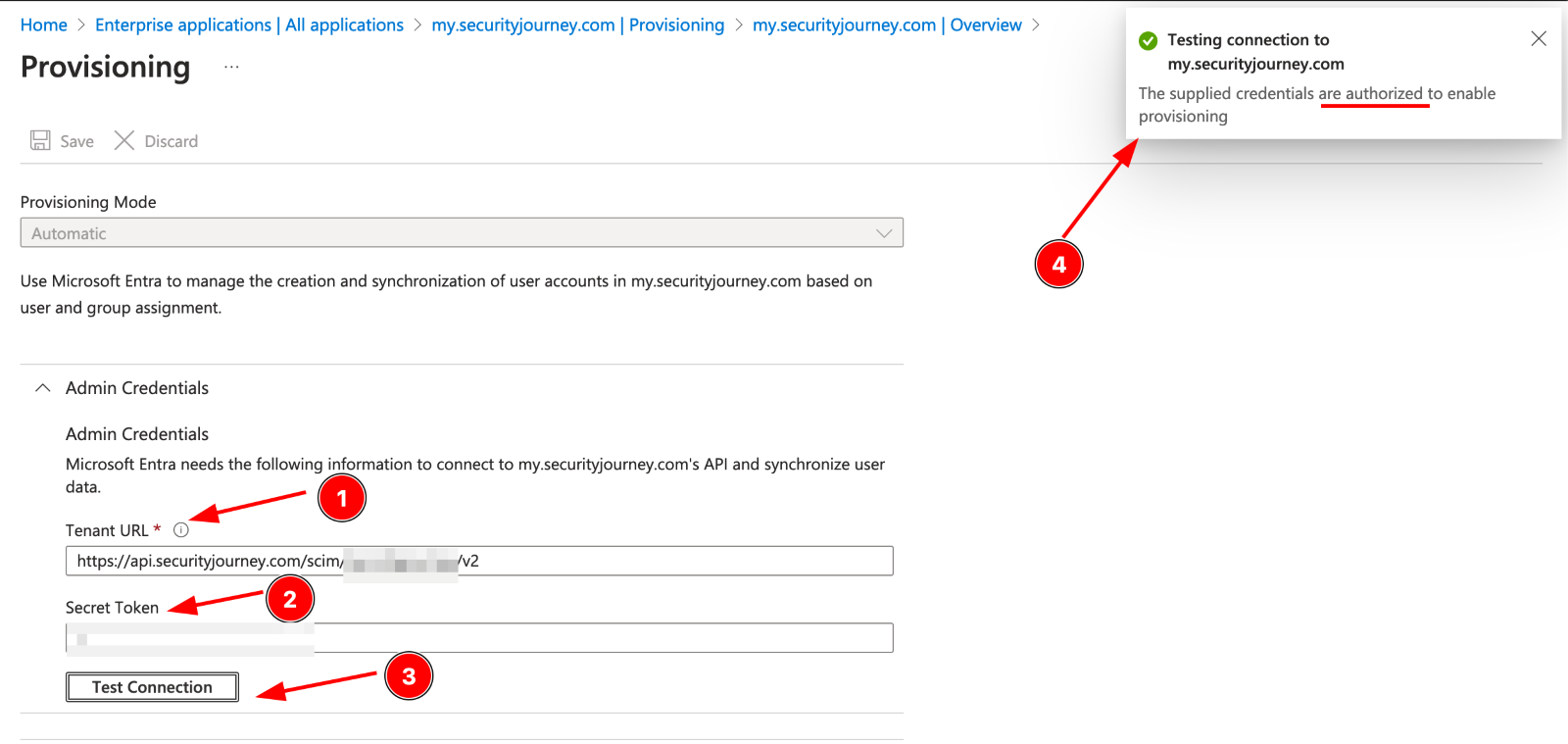
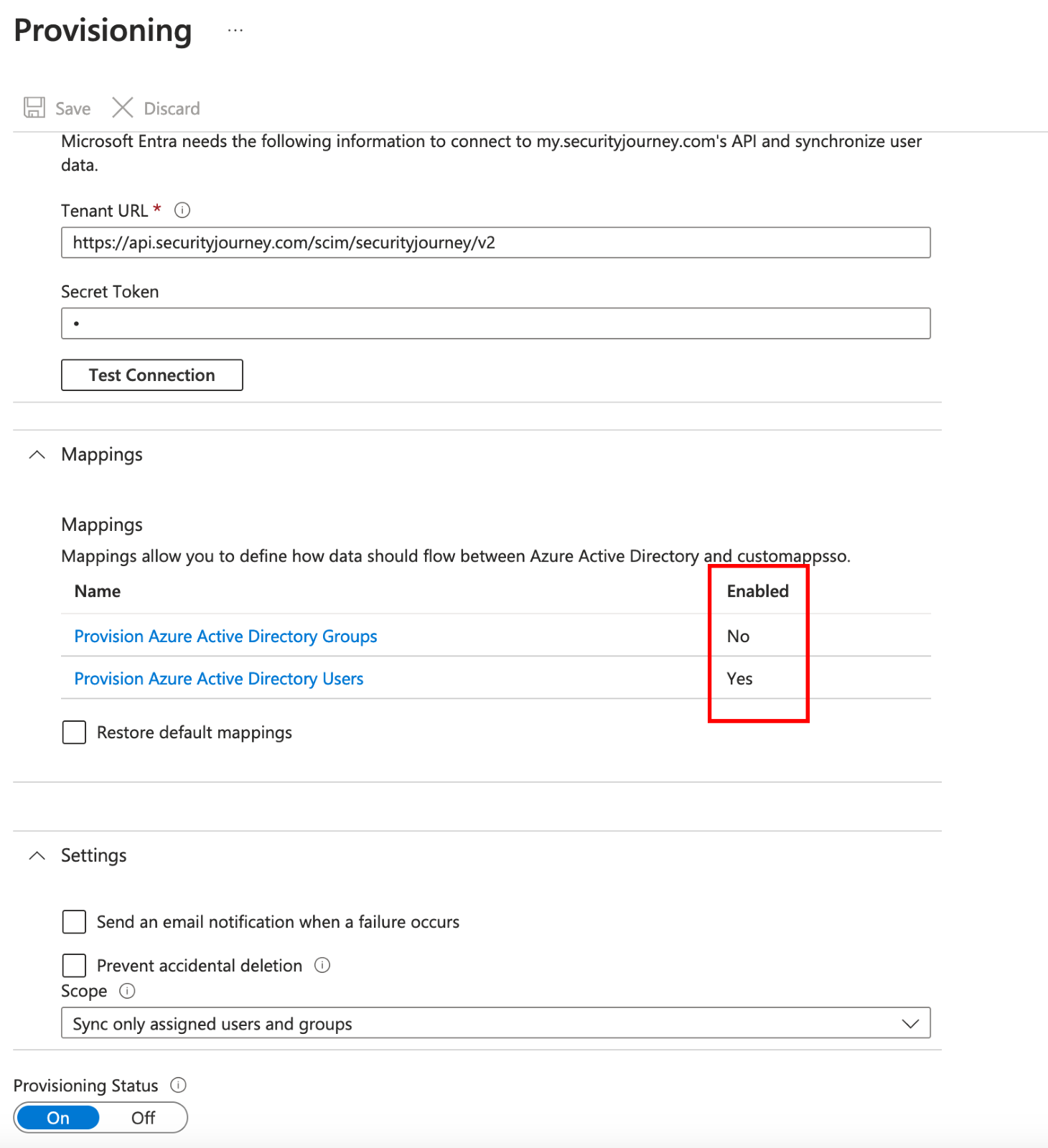
4. Under Mappings, you will need to update two settings:
-
Provision Azure Active Directory Groups - Enabled = No
-
Provision Azure Active Directory Users - Enabled = Yes
We do not support group provisioning at this time. Enabling group provisioning will result in a failed sync.
5. Update or modify Microsoft's default mappings. This includes several of our supported learner attributes:
- First Name
- Last Name
- Title
- Employee Number
- Department
If you wish to include any additional supported attributes, you will need to edit or customize them here. See learner attributes section below for schema name and details below. *Manager not currently supported via SCIM
6. Update the Provisioning Status toggle to “On” and select “Save”
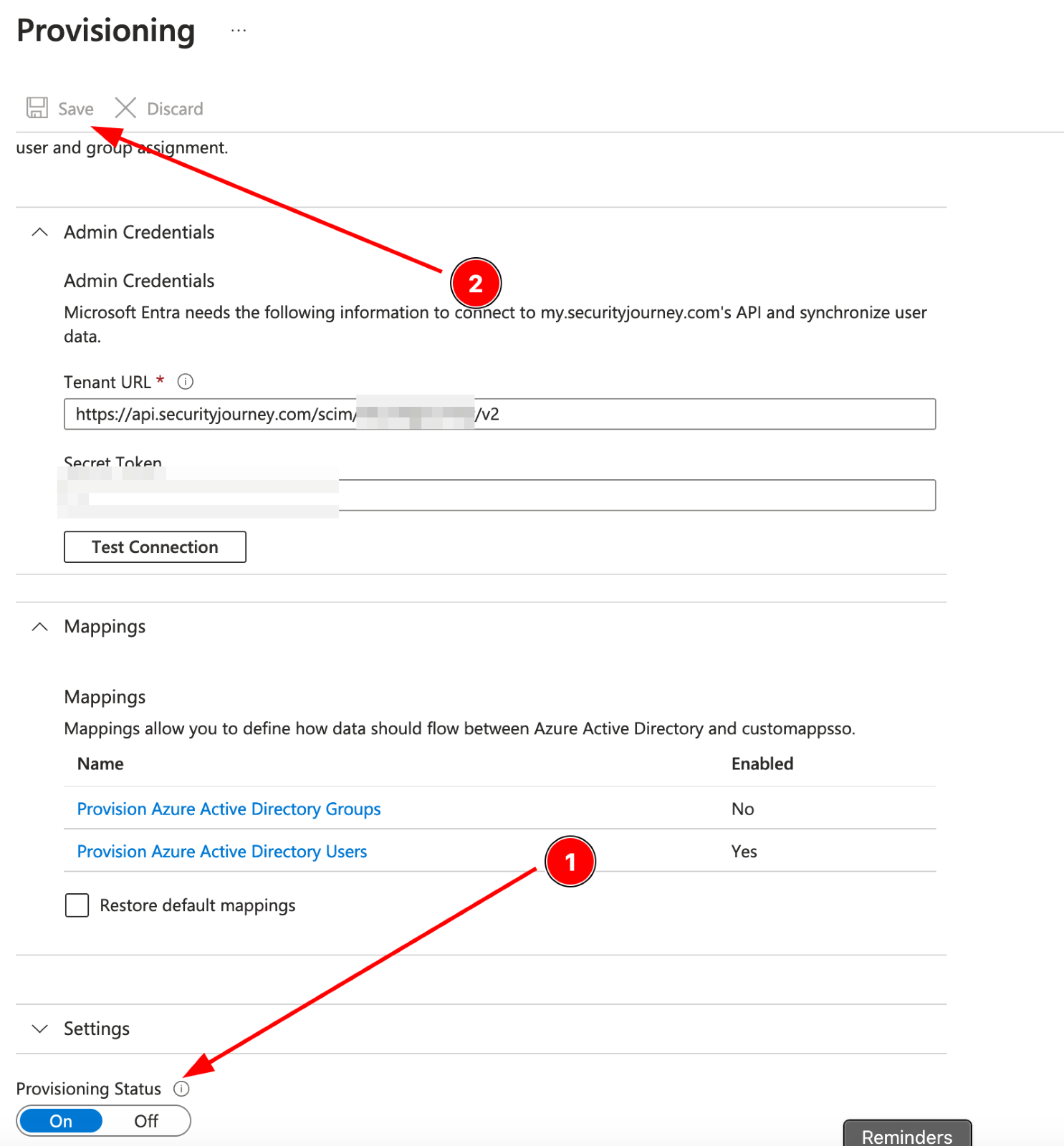
7. On the Provisioning dashboard, check that provisioning is enabled via the "Start Provisioning" play button.
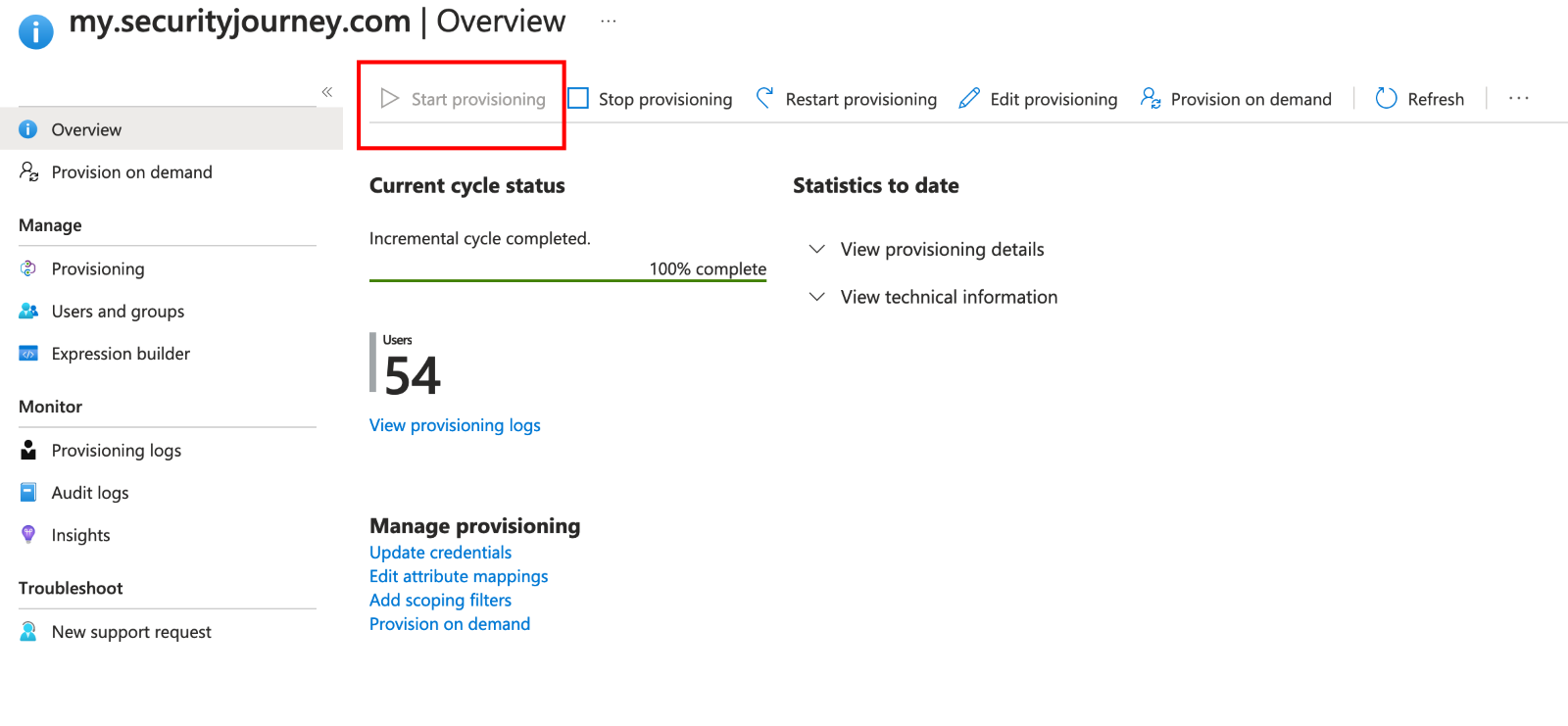
8. We recommend assigning a test user or small test group to the application first to ensure the configuration is working as expected.
-
Microsoft syncs SCIM users roughly every 20-40 minutes. At this point, grab a cup of coffee and circle back in a bit. Once it’s had a moment, please review the provisioning status, provisioning logs and audit logs for any issues.
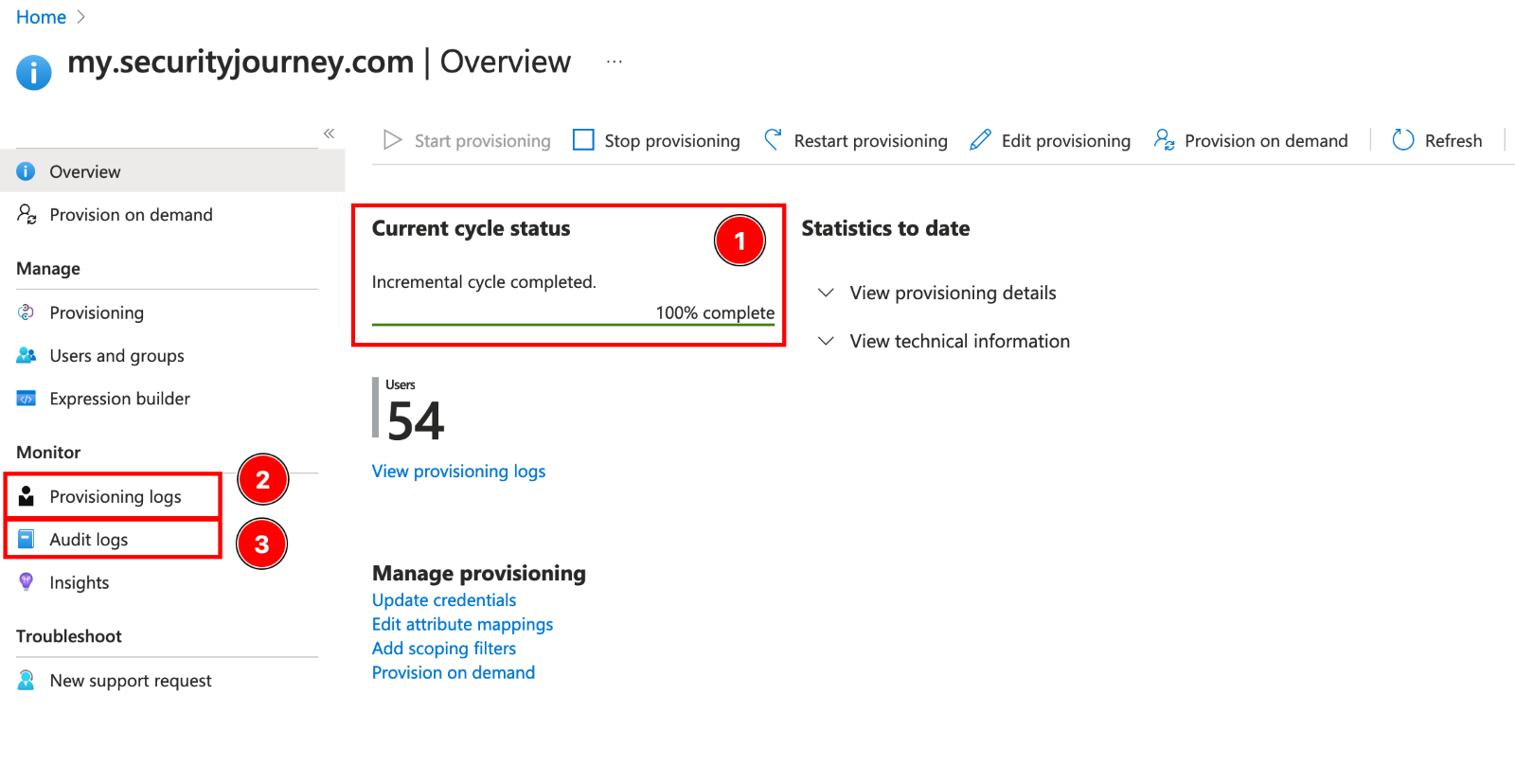
9. Once the initial sync has successfully run without unexpected errors, you can assign additional users or update your security group assignment.
Mapping Attributes
Entra required fields
The following are fields are required for a user to be created and are mapped by default.
urn:ietf:params:scim:schemas:core:2.0:Userschemauser.userName→userNameuser.firstName→name.givenNameuser.lastName→name.familyName
Enterprise user fields
The following enterprise user fields are optional and are mapped by default.
urn:ietf:params:scim:schemas:extension:enterprise:2.0:Useruser.employeeNumber→employeeNumberuser.department→department
Core user fields
The following user fields are optional and are mapped by default.
urn:ietf:params:scim:schemas:core:2.0:Useruser.title→titleuser.Country→addresses[0].country
Custom Security Journey user attributes
The following fields are custom user attributes and are NOT mapped by default.
Any value can be mapped to these fields. They can be used to populate custom assignments and used for more detailed reporting.
urn:ietf:params:scim:schemas:extension:SJUserAttributes:2.0:User- This is our custom schemajob_role- We recommend usinguser.userTypefrom the core users schema.company- We recommend usinguser.organizationfrom the enterprise user schema.business_unit- We recommend usinguser.costCenterfrom the enterprise user schema.team_name- We recommend usinguser.divisionfrom the enterprise user schema.security_champion- This is for users go above and beyond for security. We recommend setting this to the boolean value offalse.
The only attribute that is required for Security Journey is emailAddress - all other attributes are optional.
Troubleshooting
SCIM is enabled and syncing but you see this error: An HTTP/404 Not Found response was returned rather than the expected HTTP/200 OK response. To address this issue, ensure that the tenant URL is correct. The tenant URL is usually in a format like: https://<>/scim. If this does not resolve the issue, contact the application developer to ensure their SCIM endpoint conforms with the protocol https://tools.ietf.org/html/rfc7644#section-3.4.2
Please review the Provisioning settings and ensure that the Mappings settings for "Provision Azure Active Directory Groups" is set to Enabled = No.
.png)
.png)